SecureCells (
paper,
website
)
is a novel mechanism supporting application compartmentalization.
SecureCells presents a virtual memory architecture with native
support for compartments, where each processor core can track
and enforce isolation between compartments within an application.
For SecureCells, we worked on defining the correct architectural
definition of a compartment, and also implemented a RISC-V
RocketChip-based FPGA design, ported the seL4 operating system and
implemented custom example applications for the architecture.
Moving into kernel hacking,
Midas (
paper,
website
) fundamentally mitigates a common class of data-race bugs
in the Linux kernel.
Leveraging existing kernel interfaces for accessing
userspace data as well as features ubiquitous in off-the-shelf
processors, Midas creates a multi-versioning system which
prevents userspace from modifying user data while the
kernel is accessing it, thereby preventing
Time-of-Check-to-Time-of-Use (TOCTTOU) bugs.
Midas also makes it possible for system call wrapper such as
SecComp to finally validate system call arguments passed by
reference.
Going down the rabbit-hole of Speculative Execution Attacks,
SpecROP (
paper,
code
) shows how chaining speculation execution gadgets can supercharge
such attacks.
The paper proposes exploiting the CPU's existing prediction structures
to chain together two or more gadgets, allowing an attacker more
expressive computation during the speculation window.
The paper demonstrates the first attack to be able to leak a part of
the AES key during encryption.
My first project at EPFL was on characterizing and exploiting port contention
as a side-channel. The paper can be found
here. A blog post explaining the
vulnerability can be found
here.
Our proof of concept code is available
online. We were also able to
create oracles which are able to leak an SSH server's private key and
plaintext bits during AES encryption using OpenSSL.
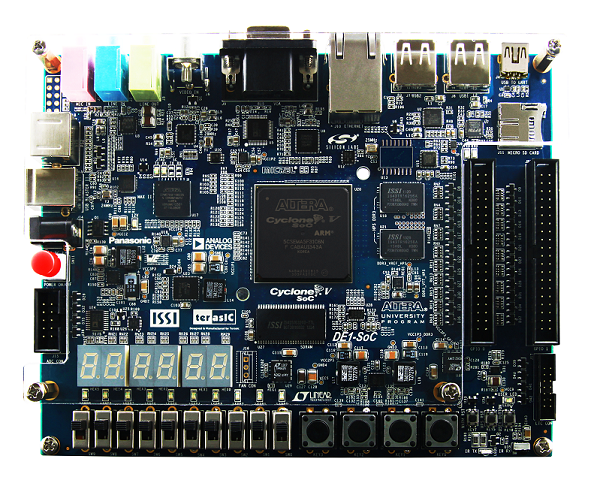
For the final project in the “Realtime Embedded Systems” course, I partnered with
Antoine Albertelli. We decided to build an audio streaming system. Our system is pretty similar in principle to what would be used in a modern radio studio. It takes an analog sound input, converts it to digital values, compresses the audio, then broadcasts over the internet. For this project, we used the DE1 board which has a dual-core ARM Cortex-A9 and an FPGA with 85K PLEs. We implemented a solution using a NIOS soft core to capture audio from a mic connected to the onboard ADC while the server ran on the hard ARM processor. The report can be found
here.
For the final project in the "Embedded Systems” course, I partnered with
Antoine Albertelli. We designed and implemented an embedded system (on a DE0-nano FPGA SoC) acquiring pictures on a TRDM-D5M camera module and sending them to an LT24 LCD module for display. The frames are stored on the HPS external RAM. They are copied from the camera and to the screen without CPU intervention using Direct Memory Access (DMA) techniques. The report can be found
here.